- Address UAE, DubaiKSA, RiyadhLevant, Amman
- Mail Ussales@nxthop.net
- Any EnquiriesUAE +971 504 537 405
KSA +966 56 139 62 22
Levant +962 787 137 119
Veridify
Cyber Protection for Automation Devices
Building Automation, Smart Buildings, Industrial Control Systems (ICS), and Critical Infrastructure
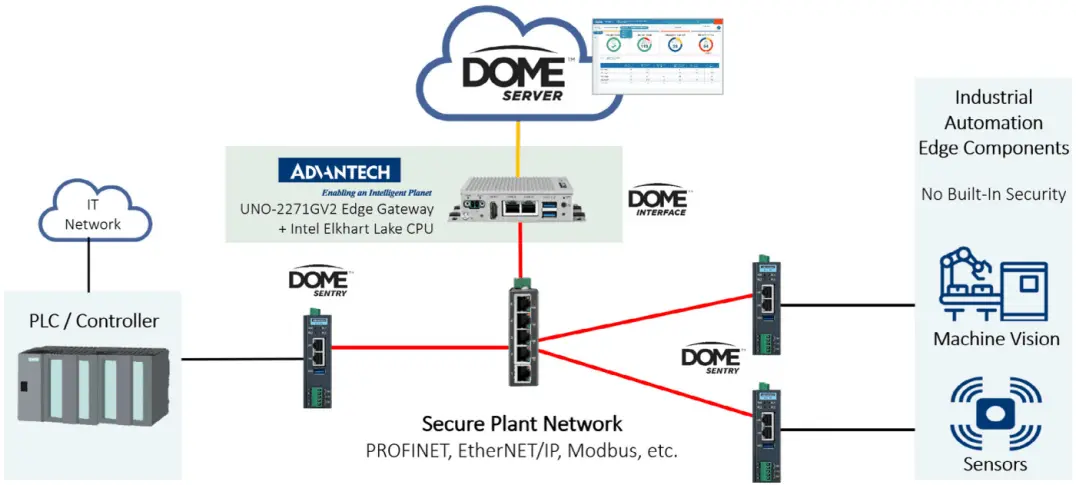
Veridify’s DOME™ solution
Delivers a flexible onboarding and ownership management blockchain platform for low-resource IoT edge devices

Veridify
Making Cyber Physical Systems and OT Networks and IT Infrastructure Cyber Safe
to Prevent Cyberattacks
Technology, Buildings, and Critical Infrastructure
DOME™ (Device Ownership Management and Enrollment™) stops cyberattacks before they can happen.