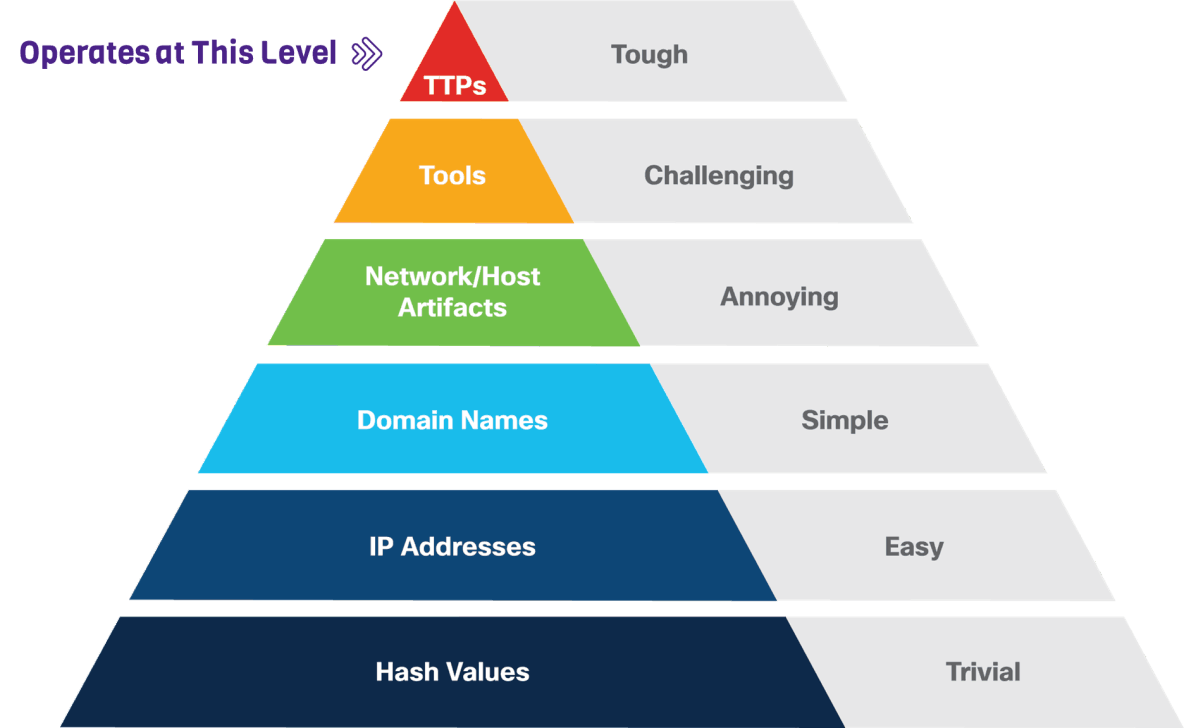
A New Way To Look At Cyber Defense
Defending against all threats is unrealistic
Identify most likely known threats that your organization faces
Understand adversarial behaviors associated with threat(s)
Test your defenses and resilience against known threats - frequently