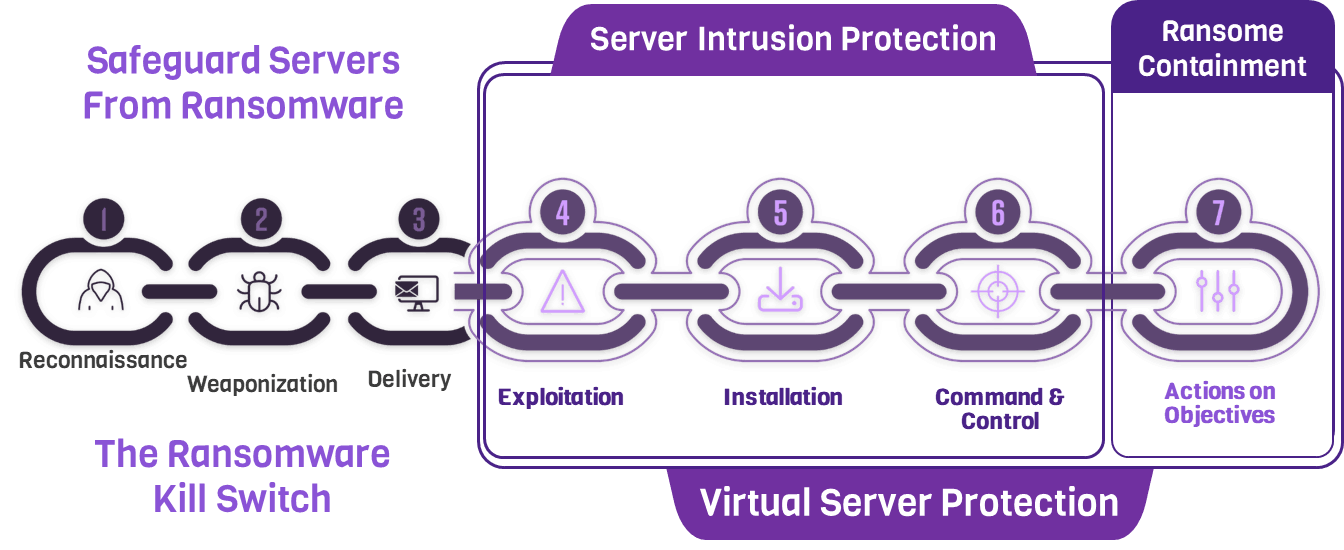
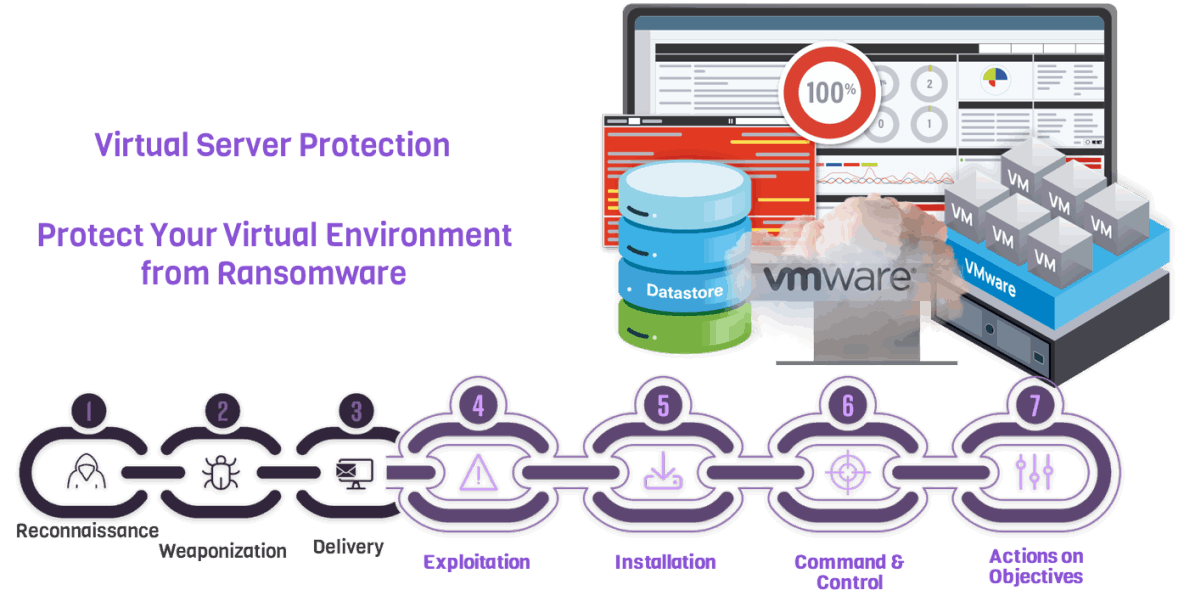
Agentless
Lightweight VM with Read-Only Permission
Fully Automated Action/Isolation
No Network or Endpoint Overhead
No Recursively Scan for Ransomware
Protect IT Critical Infrastructure Including VMware
Protect your On-Prem and Cloud Files Shares
Protect SAN/NAS, DBases App Servers and AD